Passwords#
Passwords serve different purposes in securing computer systems and protecting user data.
Terminology#
Term |
Description |
|---|---|
PIN |
A numeric code, often 4-6 characters |
Passphrase |
An alphanumeric string of characters |
Password |
Often used interchangeably with “passphrase” |
Types of passwords#
The following types of passwords and passphrases are commonly used in PureOS:
Password type |
Description |
Forgot? |
|---|---|---|
LUKS encryption passphrase |
Used to encrypt the disk and protect data at rest. Required during the boot process to unlock encrypted partitions. It is crucial to keep a backup of this passphrase in a secure location. |
|
User login PIN/passphrase |
Login credentials that a user creates to log in to their user account on the system. |
|
PureBoot user & admin PIN |
The PureBoot user PIN (used to sign boot files) and admin PIN (used to reset the signing key). |
More passwords
Password type |
Description |
Forgot? |
|---|---|---|
Librem Key user & admin PIN |
The Librem Key user PIN (regular access) and admin PIN (higher-level functions). |
|
Root password |
Used to gain administrative access to the system, if a root account is configured. |
|
Application-specific passwords |
Used to log in to specific applications, such as email clients or password managers. |
|
SSH Key passphrase |
Used to protect an SSH private key for secure remote access, if configured. |
|
Wi-Fi password |
Used to connect to secured wireless networks. |
|
Forgot your password?#
LUKS encryption passphrase#
Primary PureOS partition#
Full-disk encryption on your device means that the data on your device cannot be accessed by adversaries if they were to steal the device. Unfortunately, your system protects the data indiscriminately and cannot validate you versus an adversary without it.
Store a backup of the LUKS encryption passphrase in a secure and memorable location
Restore files from a backup if you have one
Secondary data partition#
Encrypting a secondary partition means that the data on the partition cannot be accessed by adversaries while the partition is locked. Unfortunately, your system protects the data indiscriminately and cannot validate you versus an adversary without it.
User login#
If you forget your user login password, you can reset it by booting into recovery mode or using a Live Linux install image.
Live Linux image#
Follow the following steps to reset a user password using a Live install image:
Boot into a Live Linux install image.
Launch a terminal once the Live environment has loaded.
Identify the root partition where the PureOS installation is located. Use the following command to list the partitions:
sudo fdisk -l
The partition is typically something like
/dev/sda1,/dev/sda2, etc.Create a mount point.
sudo mkdir /mnt/temp
Mount the root partition. Replace
/dev/sdaXwith the correct partition identifier you found in the previous step.sudo mount /dev/sdaX /mnt/temp
Use the
chrootcommand to change the shell environment to the mounted partition.sudo chroot /mnt/temp
Reset the user (or root) password. Replace
usernamewith the actual username of the account you want to reset.passwd usernameYou will be prompted to enter a new password for the user. Enter the new password and confirm it.
Exit the chroot environment after resetting the password:.
exitUnmount the root partition:
sudo umount /mnt/temp
Finally, reboot the system and remove the Live install disk:
sudo reboot
After the system reboots, you should be able to log in with the new password you set for the user account.
Change the disk encryption passphrase#
This guide describes how to change the passphrase of an encrypted LVM partition.
The passphrase may include numbers, symbols, and a mix of upper and lower-case characters.
Important
It is good practice to create a backup of this passphrase, as it is required every time the device is powered on.
Method 1: Using the terminal#
LUKS allows for an encrypted partition/system to have multiple passwords and also to remove them. To change the password, we first add the new password and then remove the old one.
Get the name of the encrypted volume. Launch a terminal emulator and issue the following command:
lsblk
It will show you the name of the partition. Ignore
/bootand/swap.test@test-pc:~$ lsblk NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINT sda 8:0 0 20G 0 disk ├─sda1 8:1 0 1,1G 0 part /boot ├─sda2 8:2 0 10,5G 0 part │ └─luks-92d57f72-cb7f-431e-8446-052f1d569dd3 │ 254:0 0 10,5G 0 crypt / └─sda3 8:3 0 8,4G 0 part └─luks-23b1ab2d-064e-4d58-a365-9c84a4d55cd7 254:1 1 8,4G 0 crypt [SWAP] sr0 11:1 1 1,5G 0 rom /media/test/PureOS 8.0 GNOME Live test@test-pc:~$ █Note
In this case the encrypted volume is called
sda2but your computer can have a different name. Make sure you adjusted these commands to with the name of your device!Add a new password. Issue the following command in a terminal emulator:
sudo cryptsetup luksAddKey /dev/device_name
Type the password when prompted, then press
Enter.test@test-pc:~$ sudo cryptsetup luksAddKey /dev/sda2 [sudo] password for test: █
Type the old disk encryption password when prompted, then press
Enter.test@test-pc:~$ sudo cryptsetup luksAddKey /dev/sda2 [sudo] password for test: Enter any existing passphrase: █
Type the new password for the encrypted disk, then press
Enter.test@test-pc:~$ sudo cryptsetup luksAddKey /dev/sda2 [sudo] password for test: Enter any existing passphrase: Enter new passphrase for key slot: █
Confirm the new password and press
Enter.test@test-pc:~$ sudo cryptsetup luksAddKey /dev/sda2 [sudo] password for test: Enter any existing passphrase: Enter new passphrase for key slot: Verify passphrase: █
The new password is now added.
Remove the old password. Issue the following command in a terminal emulator:
sudo cryptsetup luksRemoveKey /dev/device_name
Type the password to delete and press
Enter.
Method 2: Using GNOME Disks#
Mobile devices
Launch GNOME Disks:
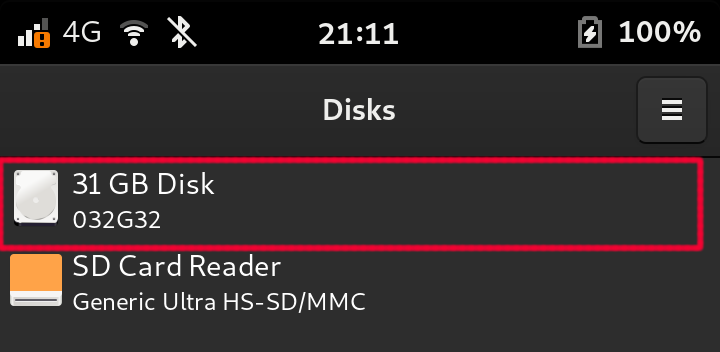
Select the storage device:
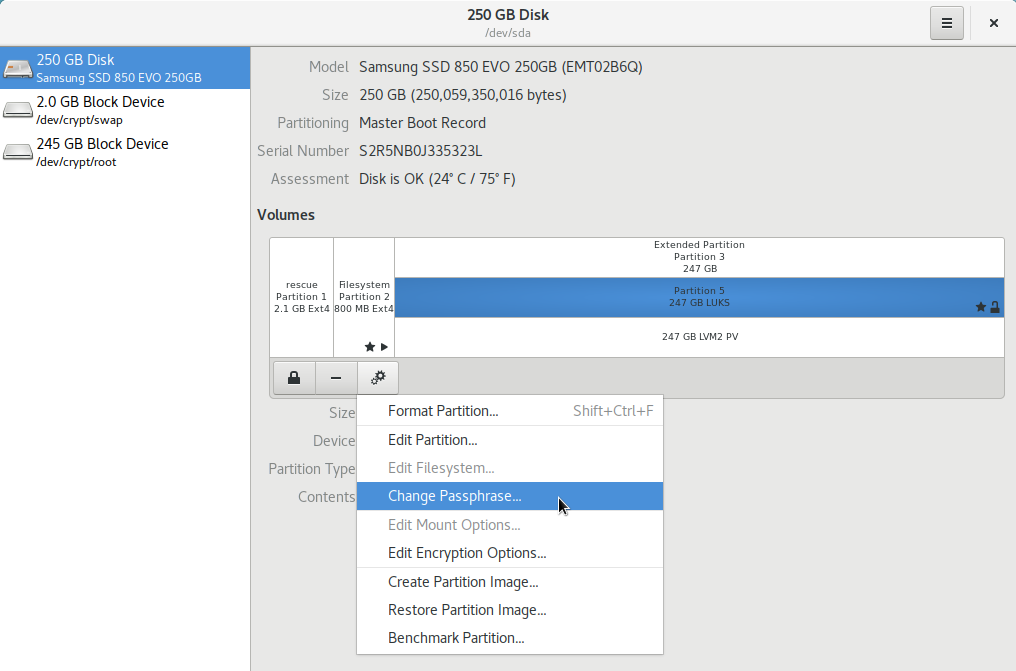
Select the LUKS partition and press the settings button:
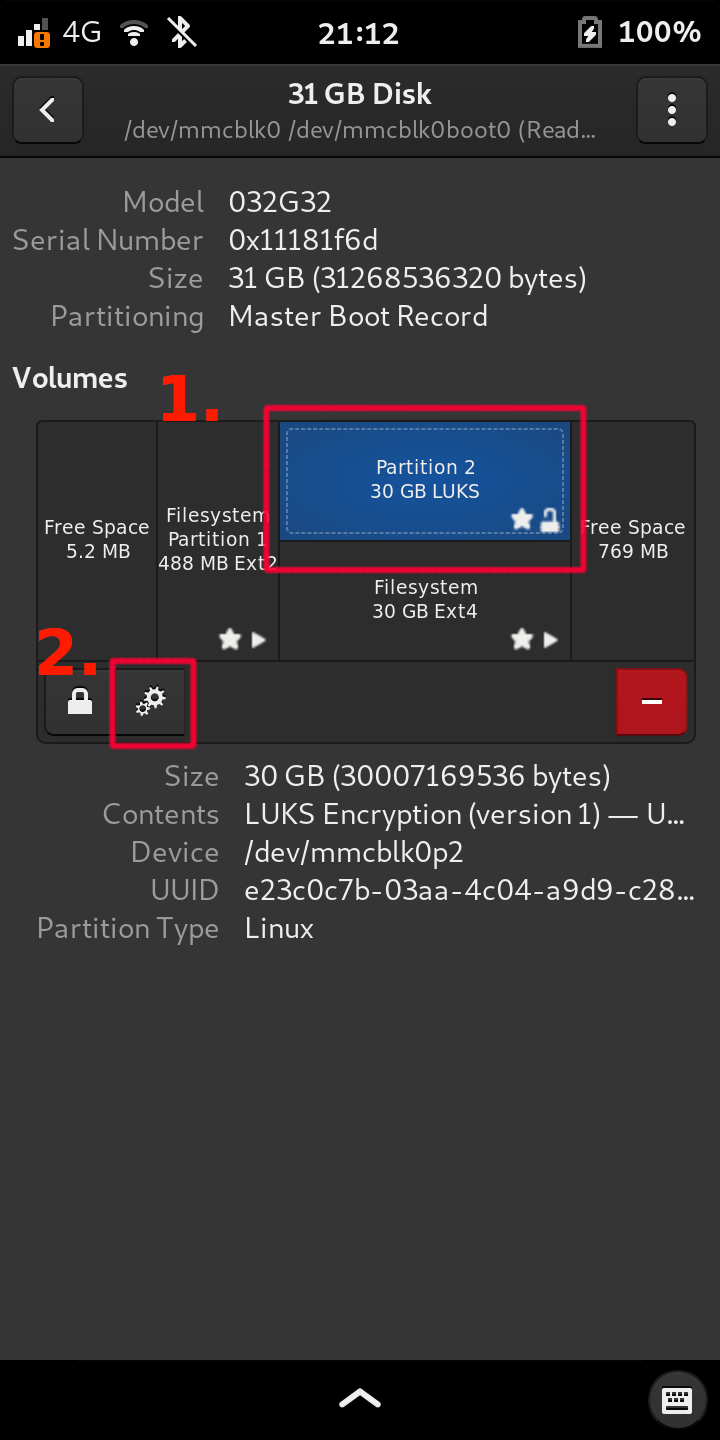
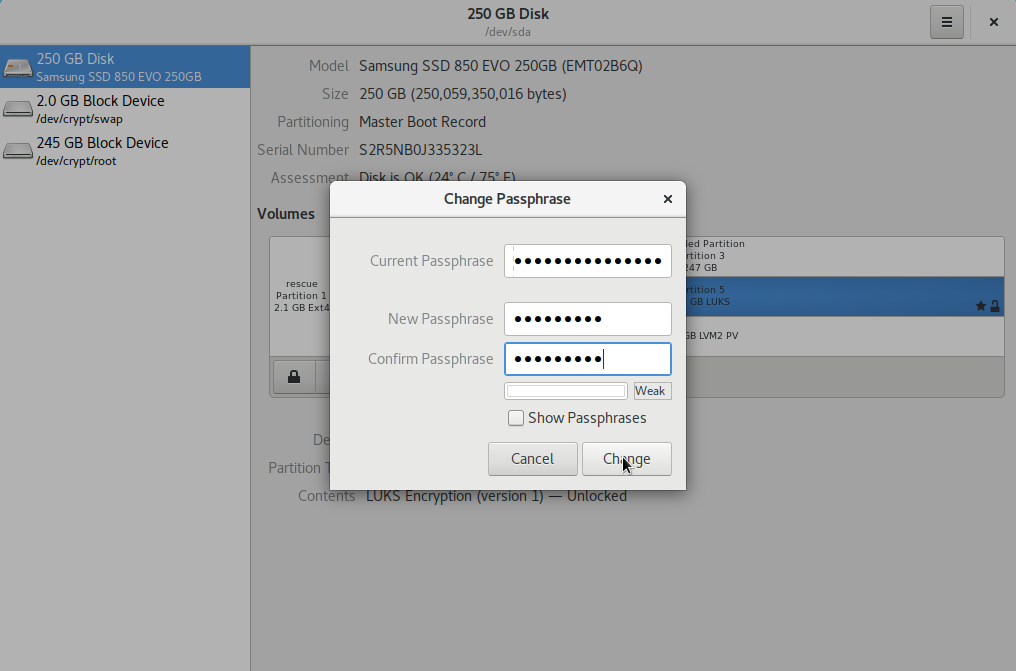
Select Change Passphrase:
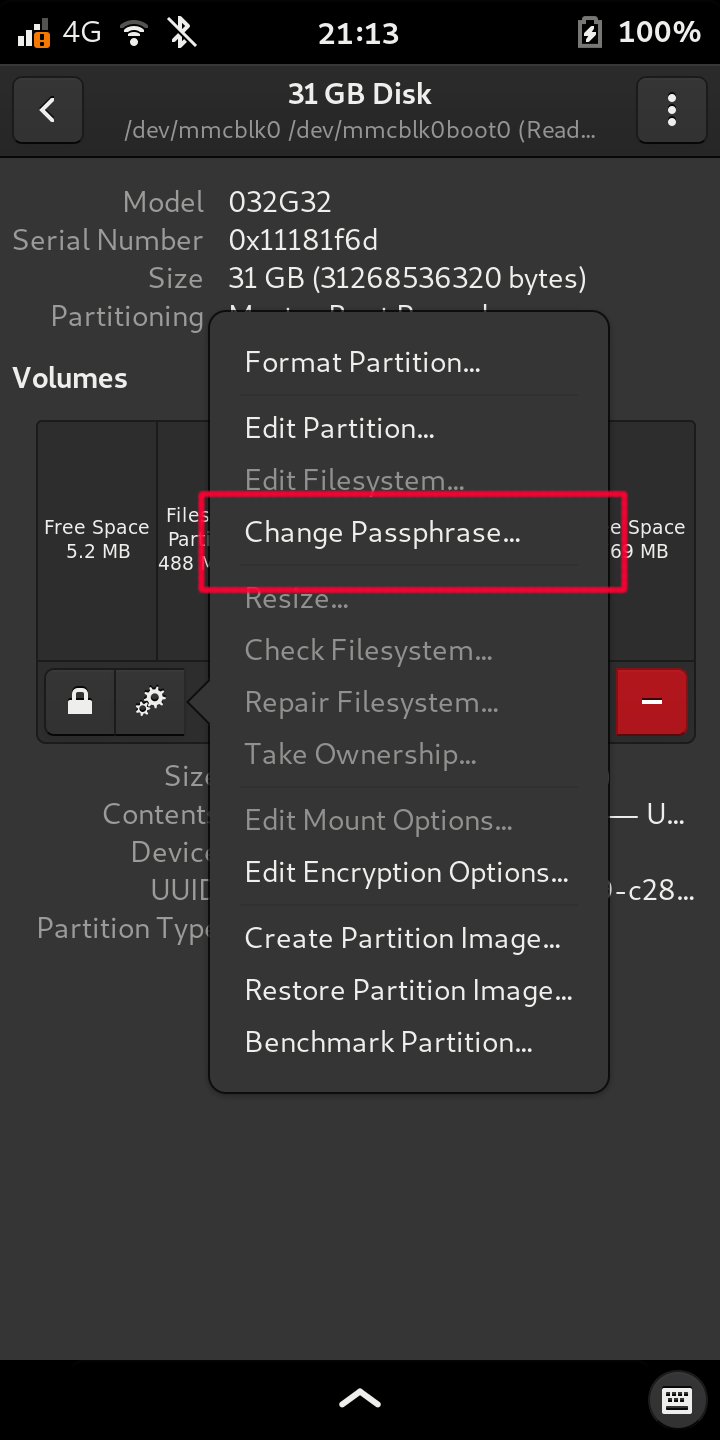
Type your
USERpassword, and press Authenticate: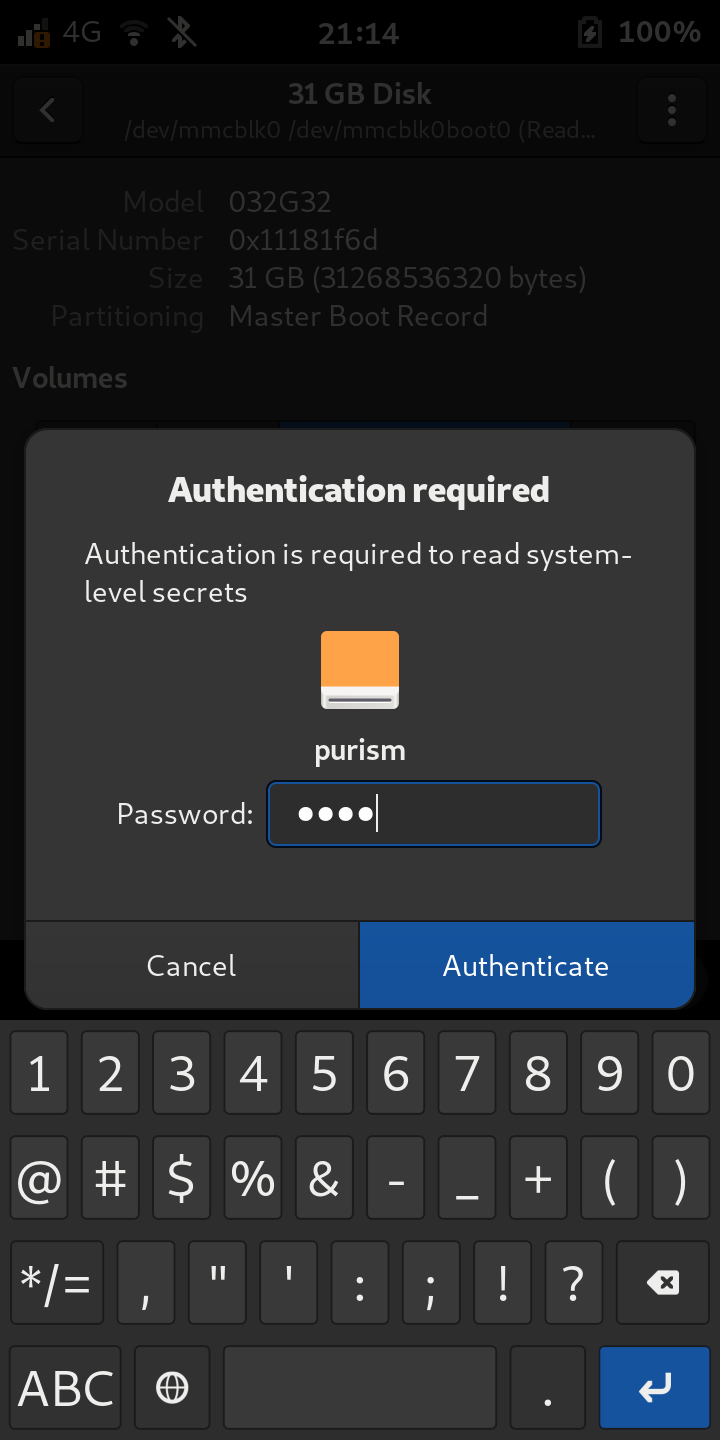
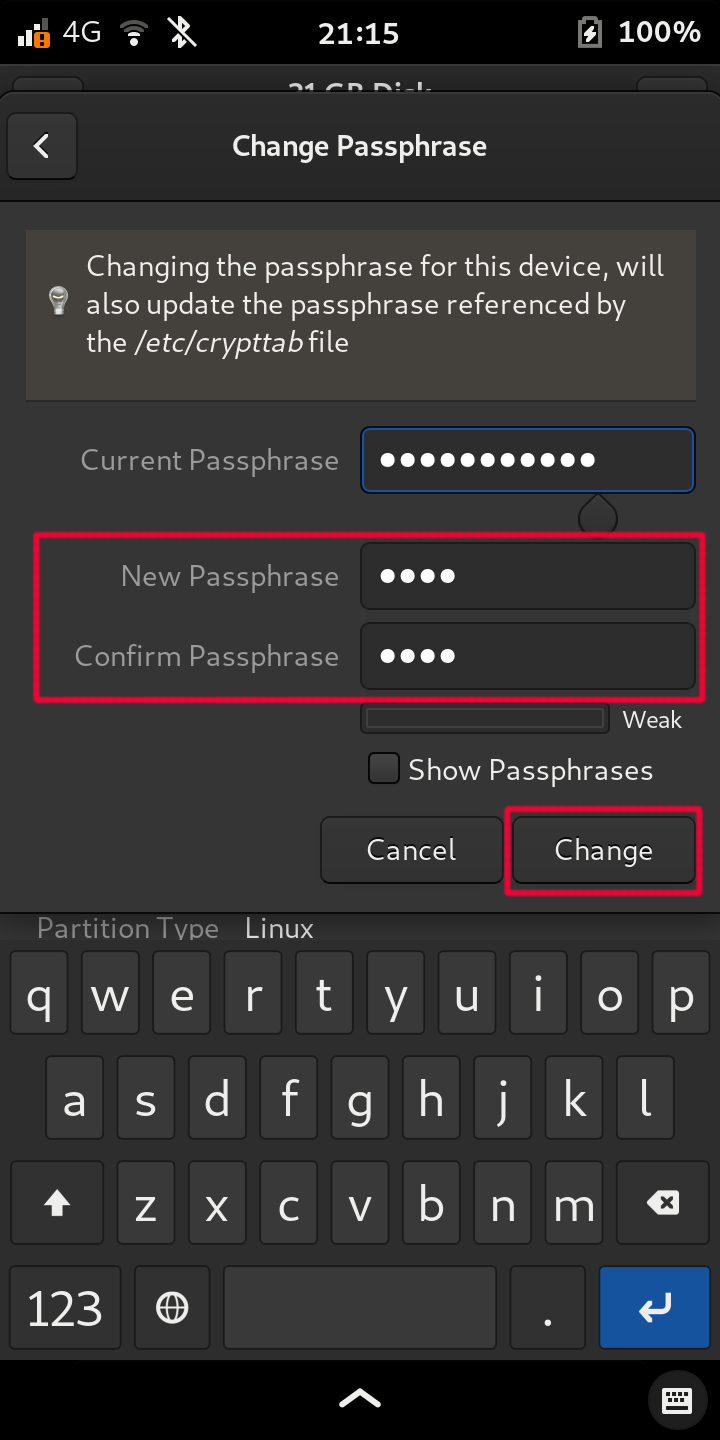
- Type in their respective fields:
Current Disk Encryption Passphrase
New Passphrase
Confirm the new Passphrase
Press Change
Change the user password#
Mobile devices
Launch the Settings application.
From the main Settings page, select Details. This opens a page describing the system software and users that have accounts on the device.
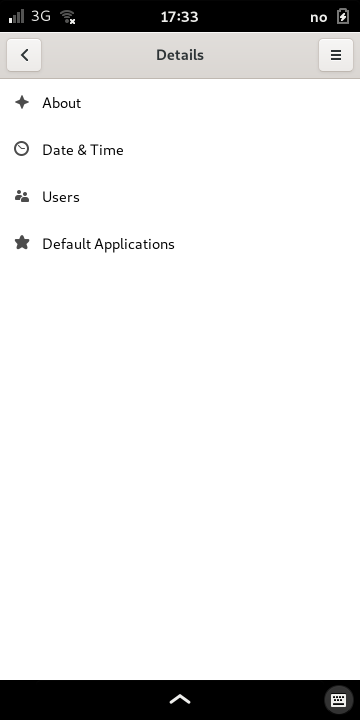
Select the Users page to view and update information about your account on the phone. This is the page you visit when you want to update the password that unlocks the phone.
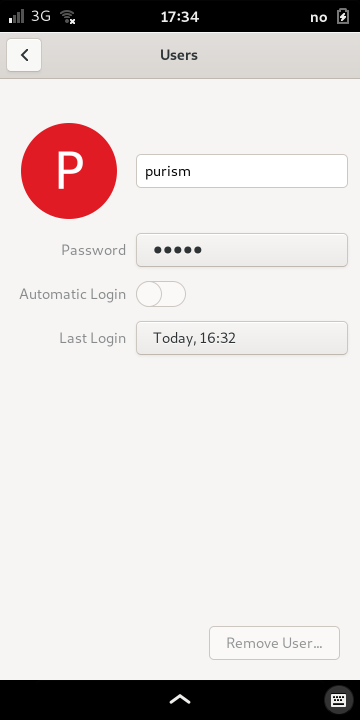
Select the button containing the hidden text next to the Password label. This will open the Change Password dialog where you will need to enter both your old password and a new one.
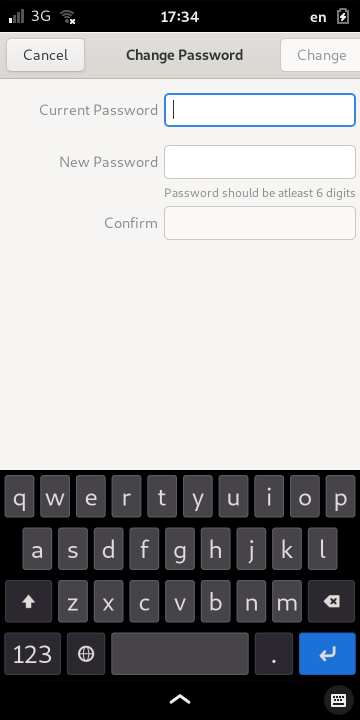
Enter the old password in the Current Password field. Then enter your new password in both the New Password and Confirm fields. This is designed to ensure that you have not mistyped your password.

When you have entered all the information, press the Change button at the top-right of the screen to confirm the change. Otherwise, press the Cancel button at the top-left of the screen to continue using your old password.
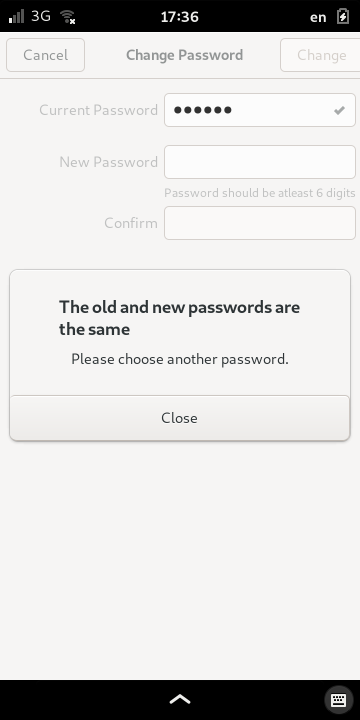
Note
You cannot use the same code for both old and new passwords. If you submit the same code for both old and new password, the system will reject the change; press Close if this occurs. Otherwise, press the Cancel button to leave the Change Password dialog and continue using the old password.
Change the root password#
Launch a terminal emulator and execute the following command:
sudo suType in your user account password and press
Enter. You are now in superuser (root) mode. You can recognize this by looking at the terminal prompt. Before entering root terminal your prompt looks something like this:username@hostname:~$
and after:
root@hostname:/home/username/
To change root password, run:
passwd
You will be prompted to
Enter new UNIX password:.Type your desired password (it will not be printed out to the screen) and press
Enter.Type it in again to confirm.
Your new root password is now set.